华为 BGP/MPLS VPN实验
哈喽,大家好!我是艺博东 ,是一个思科出身、专注于华为的网工;好了,话不多说,我们直接进入正题。
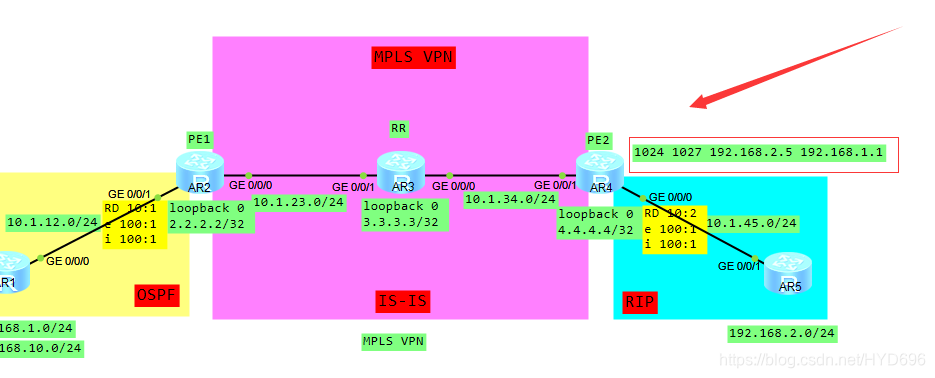
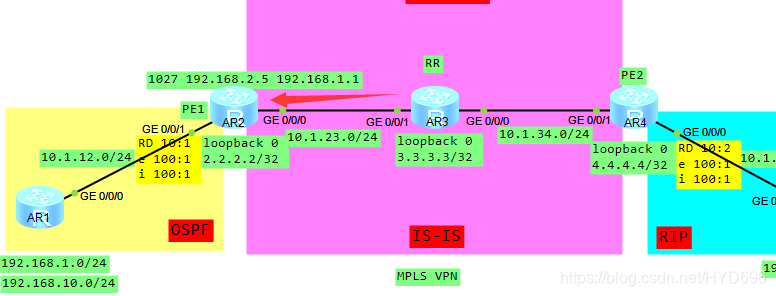
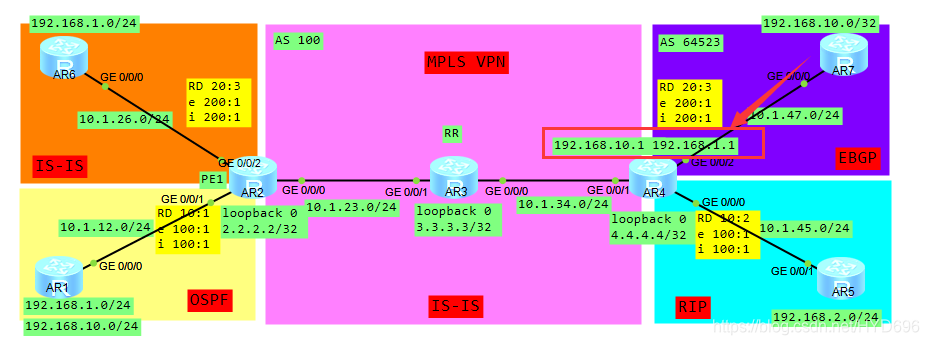
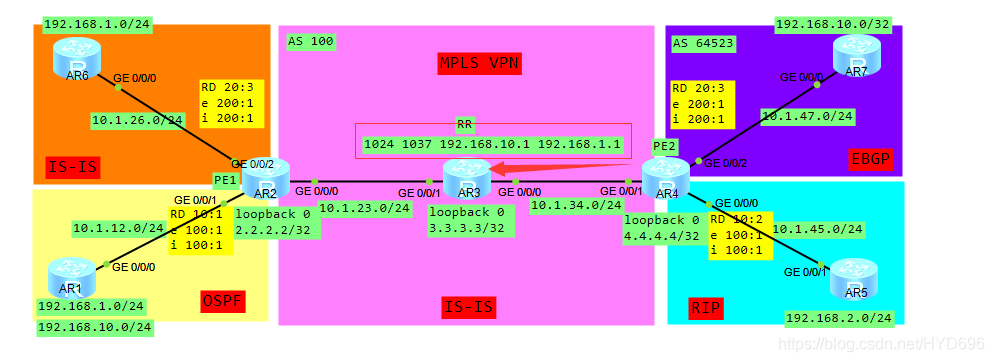
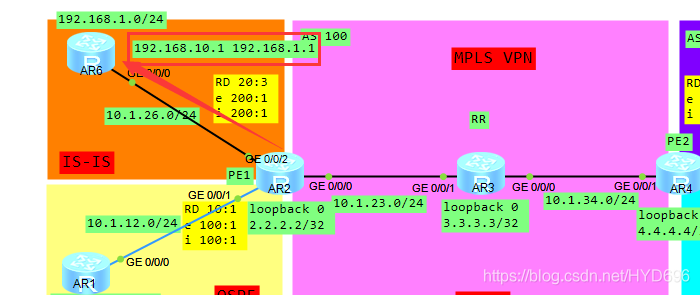
一、拓扑
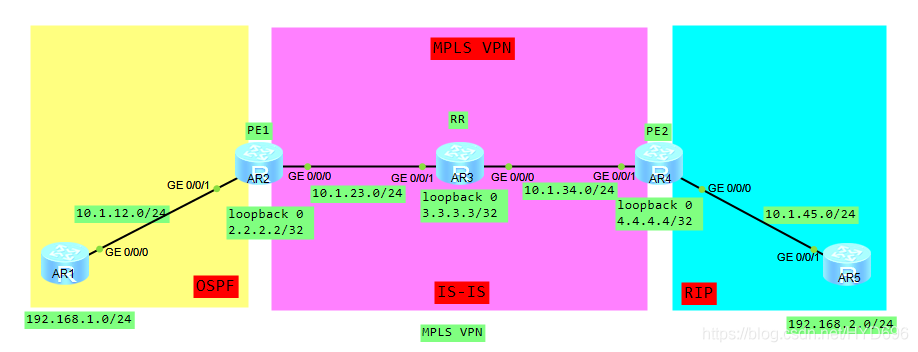
二、基础配置与分析
1、将骨干网络打通IGP
2、配置公网的LSP隧道,PE,P设备的loopack的主机路由建立LSP
3、PE之间配置MP-IBGP邻居关系(可以通过RR简化MP-IBGP全互联邻居关系)
4、VPN业务接入配置,在PE上创建VPN实例,接入用户私网路由
IS-IS
AR2
[Huawei]sysname AR2
[AR2]int l0
[AR2-LoopBack0]ip address 2.2.2.2 32
[AR2-LoopBack0]int g0/0/0
[AR2-GigabitEthernet0/0/0]ip address 10.1.23.2 24
[AR2-GigabitEthernet0/0/0]q
[AR2]isis
[AR2-isis-1]network-entity 12.0001.0000.0000.0002.00
[AR2-isis-1]is-level level-2
[AR2-isis-1]int g0/0/0
[AR2-GigabitEthernet0/0/0]isis enable
[AR2-GigabitEthernet0/0/0]int l0
[AR2-LoopBack0]isis enable
[AR2-LoopBack0]q
[AR2]int g0/0/1
[AR2-GigabitEthernet0/0/1]ip address 10.1.12.2 24- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
AR3
[Huawei]sysname AR3
[AR3]int l0
[AR3-LoopBack0]ip address 3.3.3.3 32
[AR3-LoopBack0]int g0/0/0
[AR3-GigabitEthernet0/0/0]ip address 10.1.34.3 24
[AR3-GigabitEthernet0/0/0]int g0/0/1
[AR3-GigabitEthernet0/0/1]ip address 10.1.23.3 24
[AR3-GigabitEthernet0/0/1]q
[AR3]isis
[AR3-isis-1]network-entity 12.0001.0000.0000.0003.00
[AR3-isis-1]is-level level-2
[AR3-isis-1]int l0
[AR3-LoopBack0]isis enable
[AR3-LoopBack0]int g0/0/0
[AR3-GigabitEthernet0/0/0]isis enable
[AR3-GigabitEthernet0/0/0]int g0/0/1
[AR3-GigabitEthernet0/0/1]isis enable
[AR3-GigabitEthernet0/0/1]q- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
AR4
[Huawei]sysname AR4
[AR4]int l0
[AR4-LoopBack0]ip address 4.4.4.4 32
[AR4-LoopBack0]int g0/0/1
[AR4-GigabitEthernet0/0/1]ip address 10.1.34.4 24
[AR4-GigabitEthernet0/0/1]q
[AR4]isis
[AR4-isis-1]network-entity 12.0001.0000.0000.0004.00
[AR4-isis-1]is-level level-2
[AR4-isis-1]int l0
[AR4-LoopBack0]isis enable
[AR4-LoopBack0]q
[AR4]int g0/0/1
[AR4-GigabitEthernet0/0/1]isis enable
[AR4-GigabitEthernet0/0/1]int g0/0/0
[AR4-GigabitEthernet0/0/1q
[AR4]int g0/0/0
[AR4-GigabitEthernet0/0/0]ip address 10.1.45.4 24- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
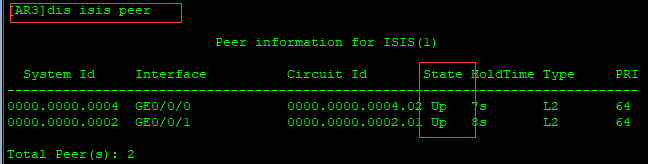
[AR3]dis isis peer
MPLS
AR2
[AR2]mpls lsr-id 2.2.2.2
[AR2]mpls
[AR2-mpls]mpls ldp
[AR2-mpls-ldp]int g0/0/0
[AR2-GigabitEthernet0/0/0]mpls
[AR2-GigabitEthernet0/0/0]mpls ldp- 1
- 2
- 3
- 4
- 5
- 6
AR3、AR4配置类似
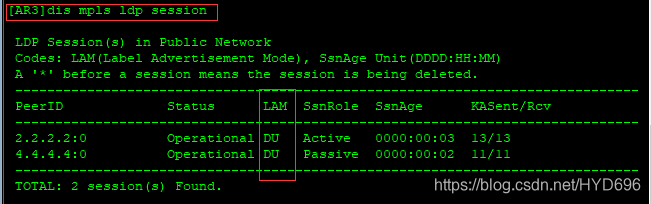
[AR3]dis mpls ldp session
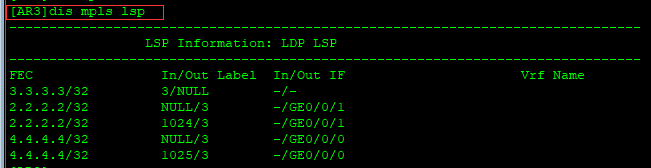
[AR3]dis mpls lsp
BGP
AR3
[AR3]bgp 100
[AR3-bgp]peer 2.2.2.2 as-number 100
[AR3-bgp]peer 2.2.2.2 connect-interface LoopBack 0
[AR3-bgp]peer 2.2.2.2 next-hop-local
[AR3-bgp]peer 4.4.4.4 as-number 100
[AR3-bgp]peer 4.4.4.4 connect-interface LoopBack 0
[AR3-bgp]peer 4.4.4.4 next-hop-local
[AR3-bgp]peer 2.2.2.2 reflect-client
[AR3-bgp]peer 4.4.4.4 reflect-client
[AR3-bgp]ipv4-family vpnv4
[AR3-bgp-af-vpnv4]peer 2.2.2.2 enable
[AR3-bgp-af-vpnv4]peer 2.2.2.2 reflect-client
[AR3-bgp-af-vpnv4]peer 4.4.4.4 enable
[AR3-bgp-af-vpnv4]peer 4.4.4.4 reflect-client - 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
AR2
[AR2]bgp 100
[AR2-bgp]peer 3.3.3.3 as-number 100
[AR2-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR2-bgp]peer 3.3.3.3 next-hop-local
[AR2-bgp]ipv4-family vpnv4
[AR2-bgp-af-vpnv4]peer 3.3.3.3 enable - 1
- 2
- 3
- 4
- 5
- 6
AR4
[AR4]bgp 100
[AR4-bgp]peer 3.3.3.3 as-number 100
[AR4-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR4-bgp]peer 3.3.3.3 next-hop-local
[AR4-bgp]ipv4-family vpnv4
[AR4-bgp-af-vpnv4]peer 3.3.3.3 enable - 1
- 2
- 3
- 4
- 5
- 6
[AR3]dis bgp peer verbose
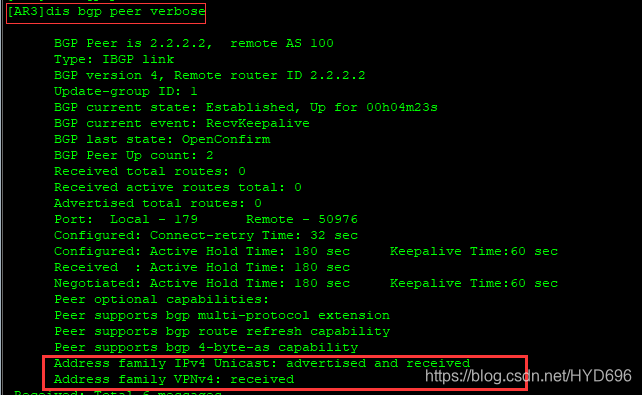
VPNv4
AR2
[AR2]bgp 100
[AR2-bgp]ipv4-family unicast
[AR2-bgp-af-ipv4]undo peer 3.3.3.3 enable- 1
- 2
- 3
AR3
[AR3]bgp 100
[AR3-bgp]ipv4-family unicast
[AR3-bgp-af-ipv4]undo peer 2.2.2.2 enable
[AR3-bgp-af-ipv4]undo peer 4.4.4.4 enable - 1
- 2
- 3
- 4
AR4
[AR4]bgp 100
[AR4-bgp]ipv4-family unicast
[AR4-bgp-af-ipv4]undo peer 3.3.3.3 enable - 1
- 2
- 3
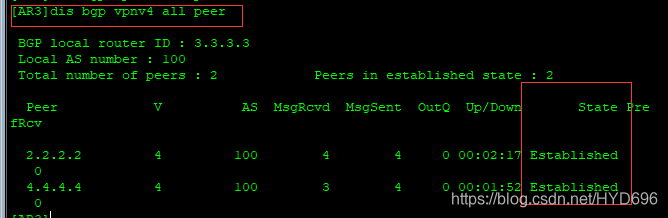
查看vpnv4地址族的BGP邻居关系
[AR3]dis bgp vpnv4 all peer dis bgp
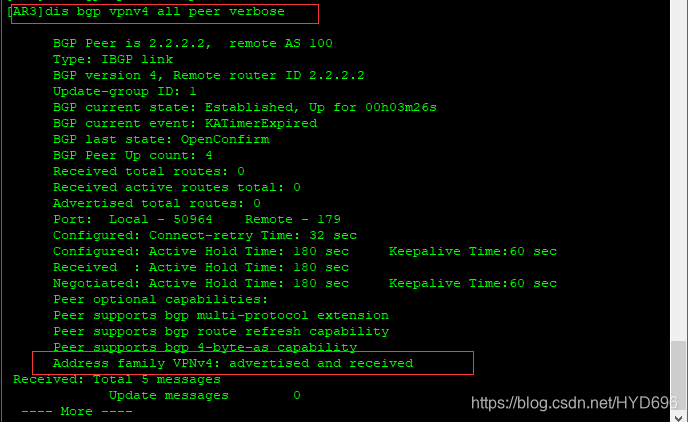
[AR3]dis bgp vpnv4 all peer verbose
VPN业务接入配置
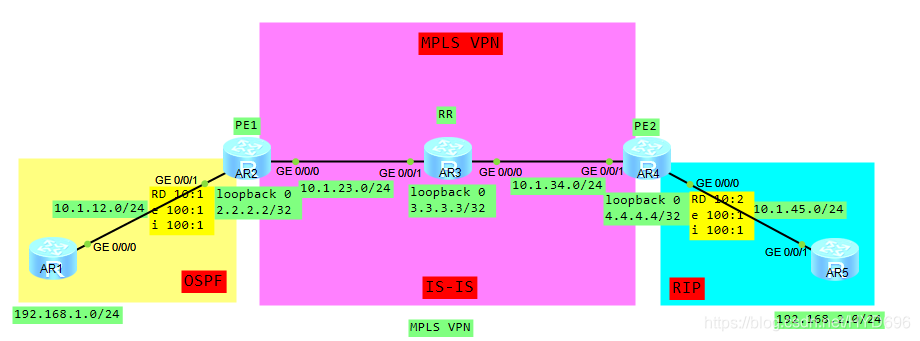
AR2
[AR2]ip vpn-instance ybd
[AR2-vpn-instance-ybd]route-distinguisher 10:1
[AR2-vpn-instance-ybd-af-ipv4]vpn-target 100:1 both
[AR2]int g0/0/1
[AR2-GigabitEthernet0/0/1]ip binding vpn-instance ybd
[AR2-GigabitEthernet0/0/1]ip address 10.1.12.2 24- 1
- 2
- 3
- 4
- 5
- 6
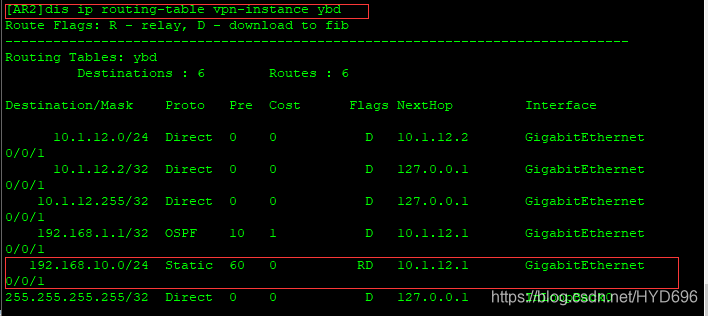
[AR2]dis ip routing-table vpn-instance ybd
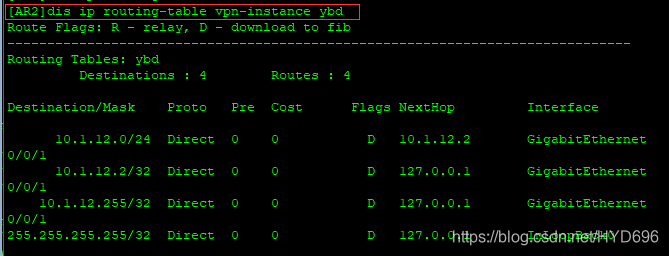
[AR2]ping -vpn-instance ybd 10.1.12.1
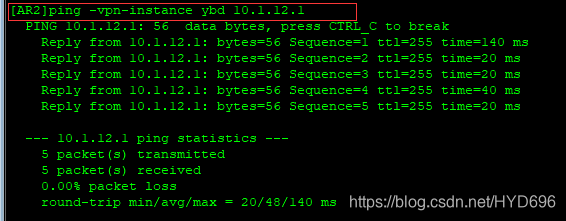
OSPF
AR1
[AR1]ospf 1 router-id 1.1.1.1
[AR1-ospf-1]a 0
[AR1-ospf-1-area-0.0.0.0]network 192.168.1.1 0.0.0.0
[AR1-ospf-1-area-0.0.0.0]network 10.1.12.1 0.0.0.0- 1
- 2
- 3
- 4
AR2
[AR2]ospf 1 vpn-instance ybd
[AR2-ospf-1]a 0
[AR2-ospf-1-area-0.0.0.0]network 10.1.12.2 0.0.0.0- 1
- 2
- 3
[AR2]dis ospf peer brief
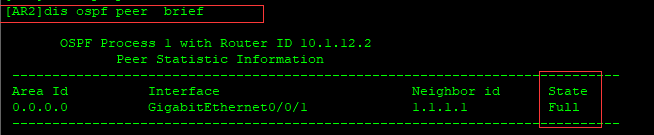
[AR2]dis ip routing-table vpn-instance ybd
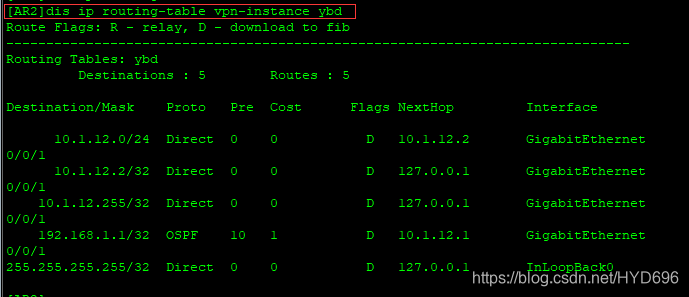
AR1、AR2
[AR1]int l10
[AR1-LoopBack10]ip address 192.168.10.1 32
[AR2]ip route-static vpn-instance ybd 192.168.10.0 24 10.1.12.1- 1
- 2
- 3
- 4
- 5
- 6
[AR2]dis ip routing-table vpn-instance ybd
RIP
AR4
[AR4]ip vpn-instance ybd6
[AR4-vpn-instance-ybd6]route-distinguisher 10:2
[AR4-vpn-instance-ybd6-af-ipv4]vpn-target 100:1 both
[AR4-vpn-instance-ybd6-af-ipv4]q
[AR4-vpn-instance-ybd6]q
[AR4]int g0/0/0
[AR4-GigabitEthernet0/0/0]ip binding vpn-instance ybd6
[AR4-GigabitEthernet0/0/0]ip address 10.1.45.4 24
[AR4-GigabitEthernet0/0/0]q
[AR4]rip 1 vpn-instance ybd6
[AR4-rip-1]version 2
[AR4-rip-1]network 10.0.0.0- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
AR5
[AR5]rip 1
[AR5-rip-1]version 2
[AR5-rip-1]network 10.0.0.0
[AR5-rip-1]network 192.168.2.0- 1
- 2
- 3
- 4
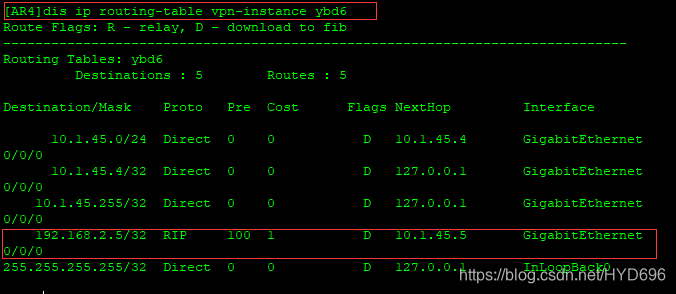
[AR4]dis ip routing-table vpn-instance ybd6
VPN业务接入配置
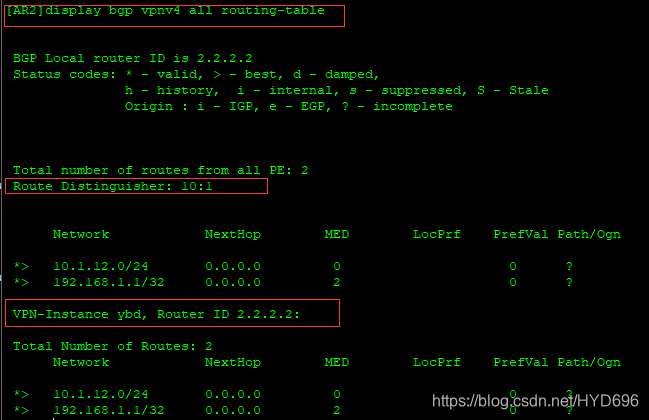
vpn-instacen ybd 路由 ---> vpn-instance vpnv4 路由 ---> vpn-insance Ai vpnv4 BGP路由
AR2
[AR2]bgp 100
[AR2-bgp]ipv4-family vpn-instance ybd
[AR2-bgp-ybd]import-route ospf 1
[AR2-bgp-ybd]import-route static - 1
- 2
- 3
- 4
[AR2]display bgp vpnv4 all routing-table
在AR2的G0/0/0接口进行抓包
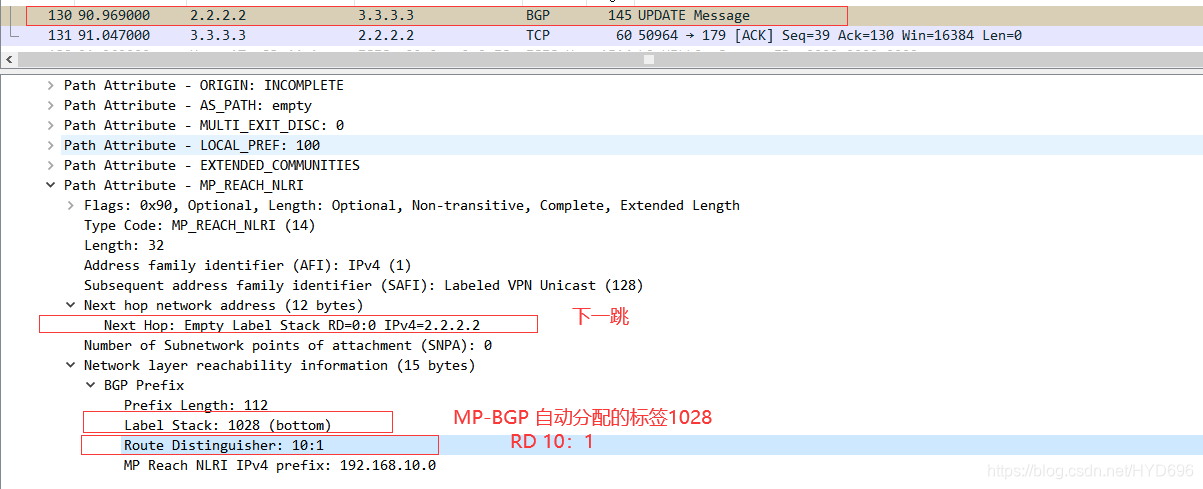
policy vpn-target 开启基于RT属性VPNv4路由的过滤
1、如果本路由器没有VPN实例业务接入,则丢弃所有vpnv4路由
2、如果本路由器存在VPN实例业务接口,则对ert和本端所有VPN实例的irt做匹配,如果ert没有和任何一个本端vpn实例的irt匹配,则丢弃。
[AR3-bgp]dis bgp vpnv4 all routing-table
没bgp vpnv4路由
RR上
[AR3-bgp]ipv4-family vpnv4
[AR3-bgp-af-vpnv4]undo policy vpn-target - 1
- 2
[AR3-bgp-af-vpnv4]dis bgp vpnv4 all routing-table
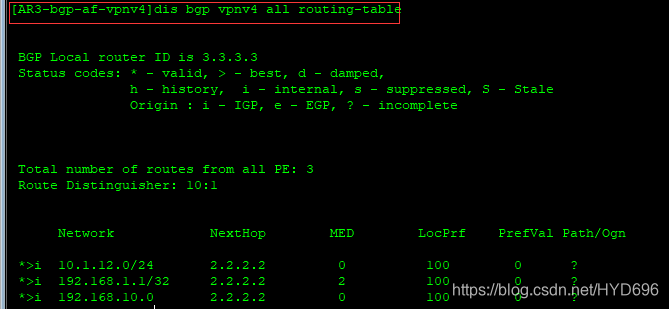
[AR4]dis bgp vpnv4 all routing-table
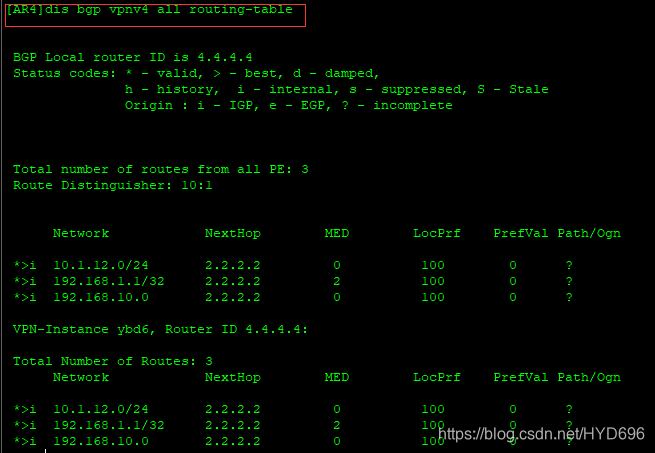
AR4已接收相应的路由。
[AR4]dis ip routing-table vpn-instance ybd6 protocol bgp
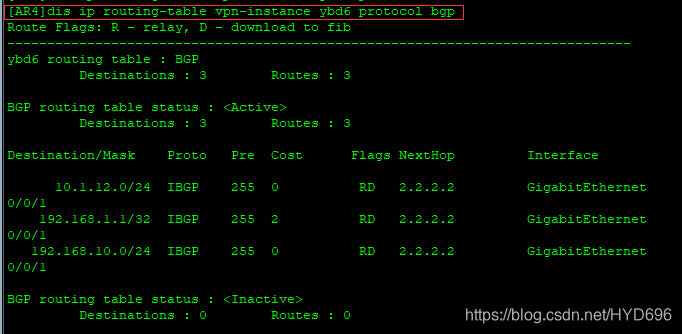
最有路由。
AR4
[AR4]bgp 100
[AR4-bgp]ipv4-family vpn-instance ybd6
[AR4-bgp-ybd6]import-route rip 1
[AR4-rip-1]import-route bgp- 1
- 2
- 3
- 4
- 5
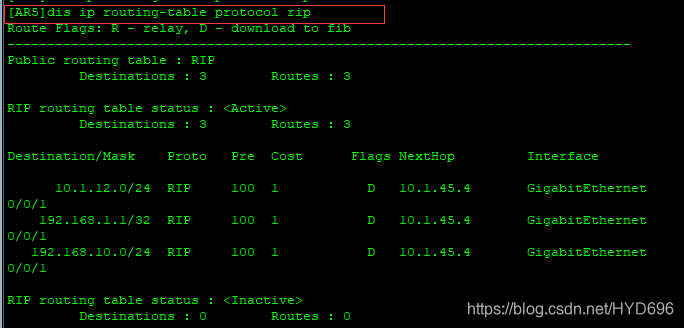
[AR5]dis ip routing-table protocol rip
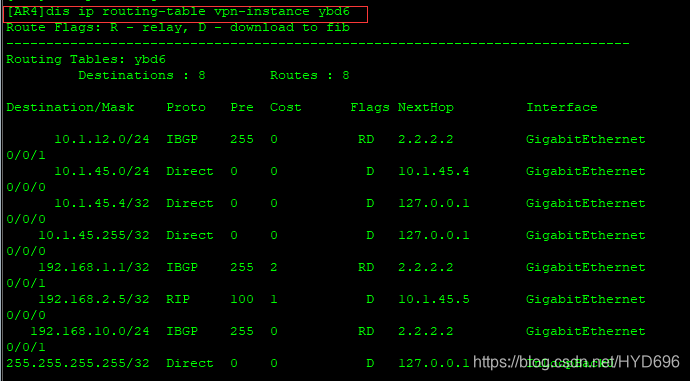
[AR4]dis ip routing-table vpn-instance ybd6
 AR2
AR2
[AR2]ospf
[AR2-ospf-1]import-route bgp- 1
- 2
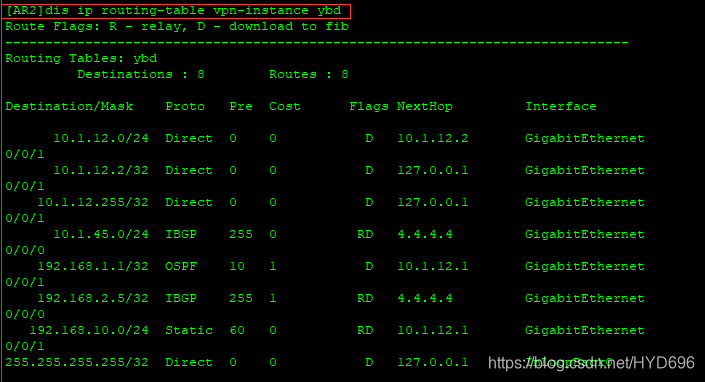
[AR2]dis ip routing-table vpn-instance ybd
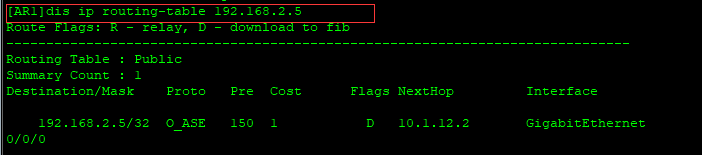
[AR1]dis ip routing-table 192.168.2.5
下面说一下AR5的192.168.2.5是怎么访问AR1的192.168.1.1的路由。
AR5查找路由表192.168.1.1,发现下一跳是10.1.45.4
然后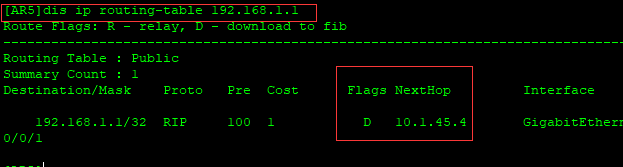
然后根据AR4的接口下绑定的ybd6路由表,去查相关路由。
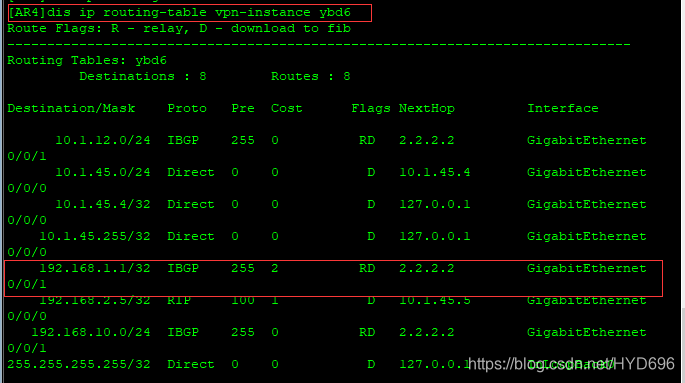
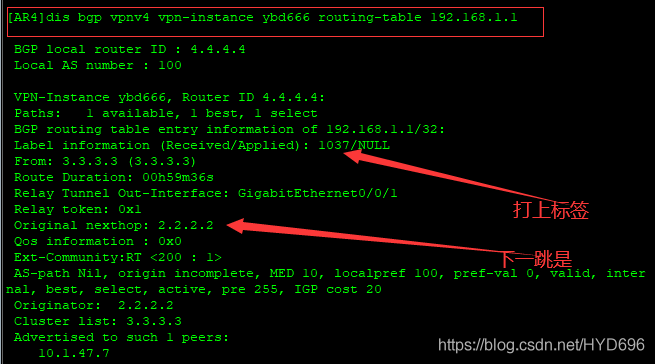
[AR4]dis bgp vpnv4 vpn-instance ybd6 routing-table 192.168.1.1
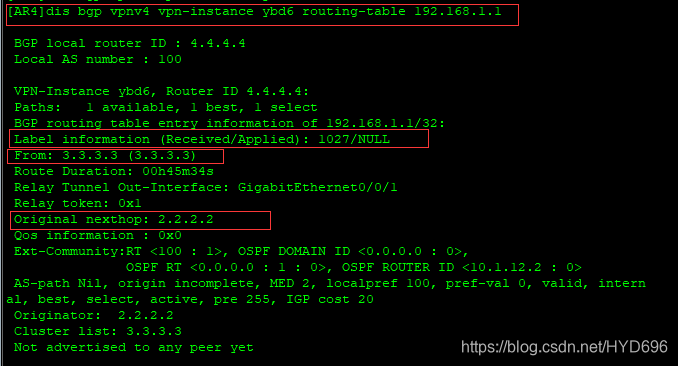
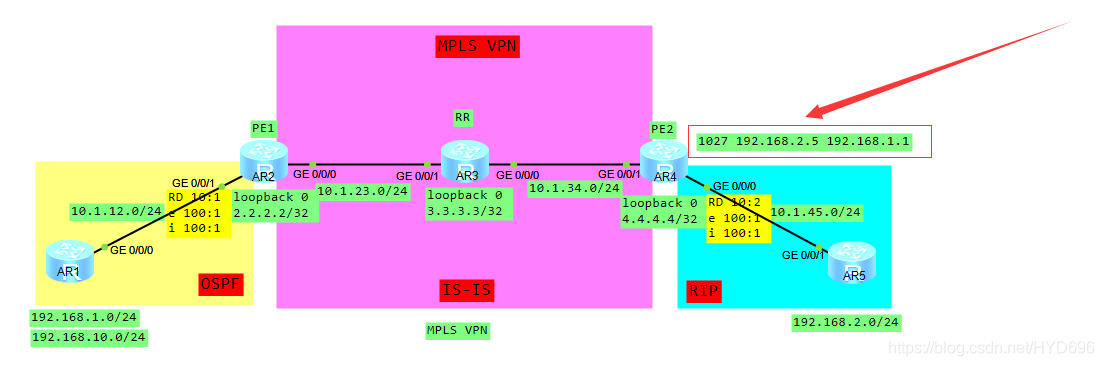
数据封装成
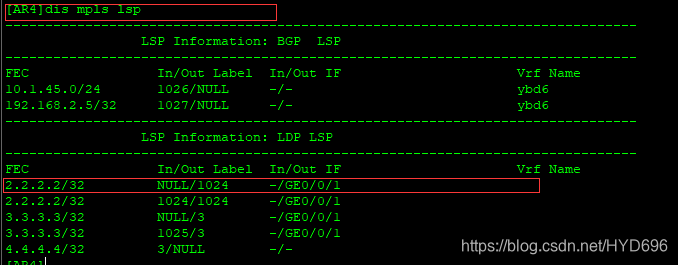
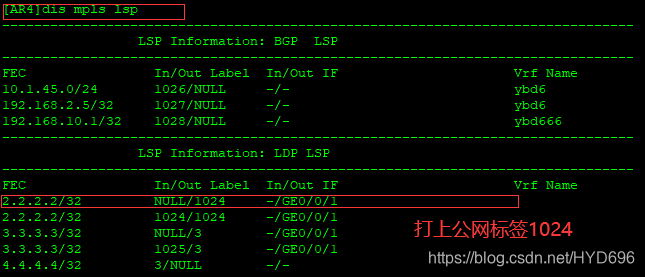
出去的标签是1024
然后数据封装成这样了
压入标签为2个。
然后AR4根据G0/0/1接口发出去,
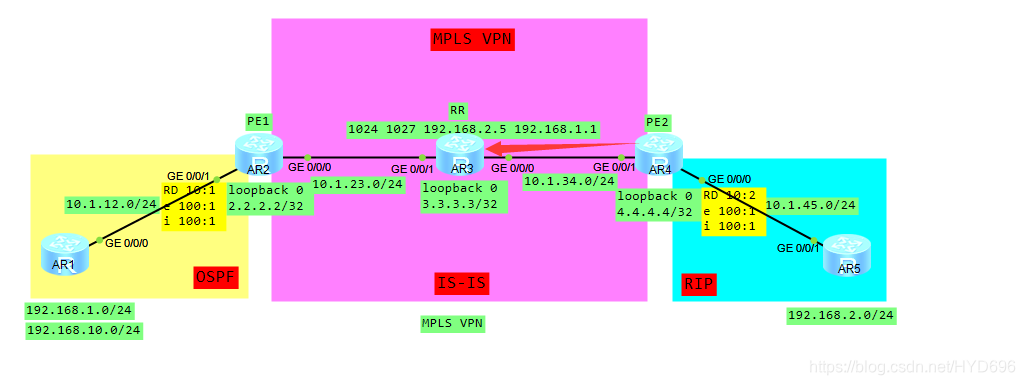
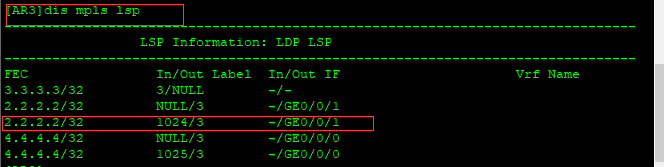
RR 查找标签
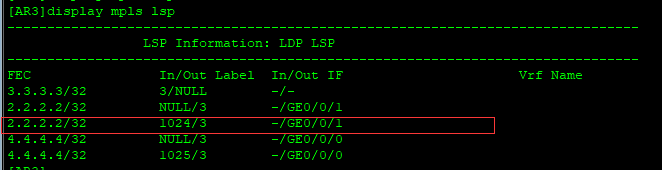
2.2.2.2的进标签1024,出标签是3,然后进行弹出顶部标签,从G0/0/1接口发送出去。
AR2收到后,查看lsp
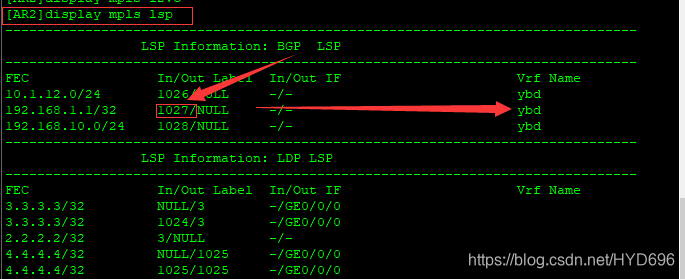
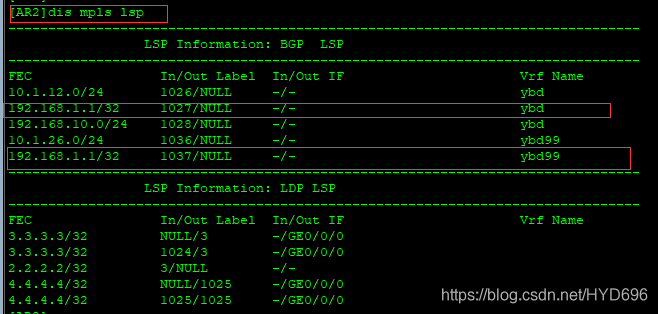
通过BGP协议得到的标签,收到的标签如果是1027的话,就属于ybd路由表进行转发的。
弹出标签
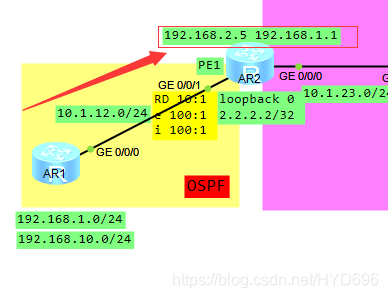
192.168.1.1属于ybd本地的报文
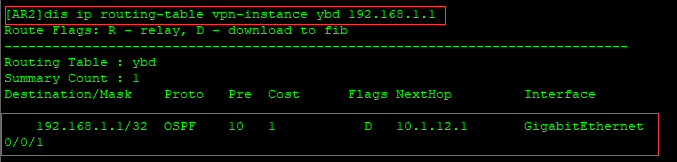
从接口g0/0/1发出,下一跳是10.1.12.1。
反过来也是一样的。
创建一个telnet
AR5
[AR5]user-interface vty 0 4
[AR5-ui-vty0-4]set authentication password cipher ybd666666
[AR5-ui-vty0-4]user privilege level 15- 1
- 2
- 3
telnet -a 192.168.1.1 192.168.2.5
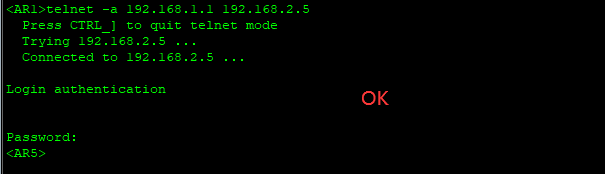
模拟内网冲突的场景,路由冲突的时候怎么区分?
拓扑
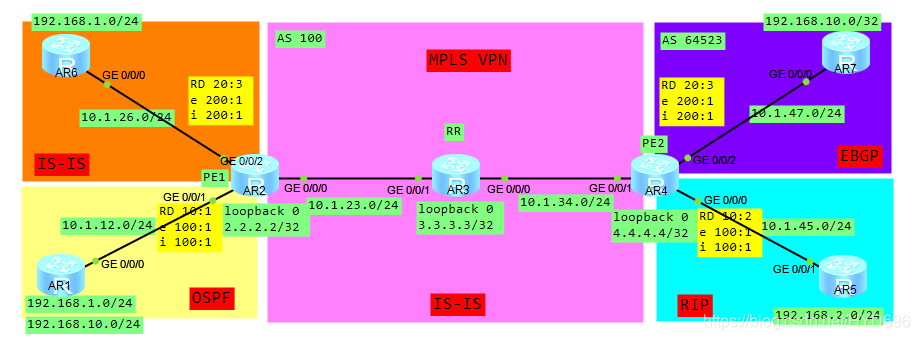
本地路由一样是可以通过VPN实例来进行区分的。
RD:区分实例,标记路由,只在本地有效,区分不同站点的相同路由;
RT:对路由进行控制,控制路由的导入与导出。
注意:可以是相同的DR的
AR2
[AR2]int g0/0/2
[AR2-GigabitEthernet0/0/2]ip address 10.1.26.2 24
[AR2]ip vpn-instance ybd99
[AR2-vpn-instance-ybd99]route-distinguisher 20:3
[AR2-vpn-instance-ybd99]vpn-target 200:1 both
[AR2]int g0/0/2
[AR2-GigabitEthernet0/0/2]ip binding vpn-instance ybd99
[AR2-GigabitEthernet0/0/2]ip address 10.1.26.2 24
[AR2]isis 10 vpn-instance ybd99
[AR2-isis-10]is-level level-2
[AR2-isis-10]network-entity 12.0099.0000.0000.0002.00
[AR2-isis-10]int g0/0/2
[AR2-GigabitEthernet0/0/2]isis enable 10- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
AR6
[Huawei]sysname AR6
[AR6]int g0/0/0
[AR6-GigabitEthernet0/0/0]ip address 10.1.26.6 24
[AR6-LoopBack0]ip address 192.168.1.1 32
[AR6]isis
[AR6-isis-1]network-entity 12.0099.0000.0000.0006.00
[AR6-isis-1]is-level level-2
[AR6-isis-1]int g0/0/0
[AR6-GigabitEthernet0/0/0]isis enable
[AR6-GigabitEthernet0/0/0]int l0
[AR6-LoopBack0]isis enable
[AR2]bgp 100
[AR2-bgp]ipv4-family vpn-instance ybd99
[AR2-bgp-ybd99]import-route isis 10- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
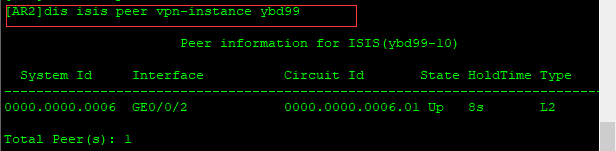
[AR6]dis isis peer
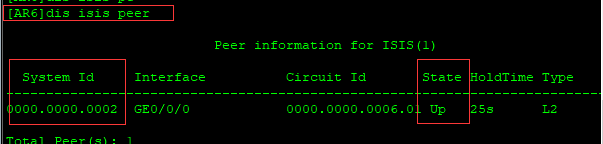
[AR2]dis isis peer vpn-instance ybd99
AR4
[AR4]ip vpn-instance ybd666
[AR4-vpn-instance-ybd666]route-distinguisher 20:3
[AR4-vpn-instance-ybd666-af-ipv4]vpn-target 200:1 both
[AR4-vpn-instance-ybd666-af-ipv4]int g0/0/2
[AR4-GigabitEthernet0/0/2]ip binding vpn-instance ybd666
[AR4-GigabitEthernet0/0/2]ip address 10.1.47.4 24
[AR4]bgp 100
[AR4-bgp]ipv4-family vpn-instance ybd666
[AR4-bgp-ybd666]peer 10.1.47.7 as 64523- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
华为设备当将BGP路由引入到IGP时,只将EBGP路由引入。
AR7
[Huawei]sysname AR7
[AR7]int l0
[AR7-LoopBack0]ip address 192.168.10.1 32
[AR7-LoopBack0]int g0/0/0
[AR7-GigabitEthernet0/0/0]ip address 10.1.47.7 24
[AR7]bgp 64523
[AR7-bgp]peer 10.1.47.4 as 100
[AR7-bgp]network 192.168.10.1 32- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
[AR4]dis bgp vpnv4 all peer
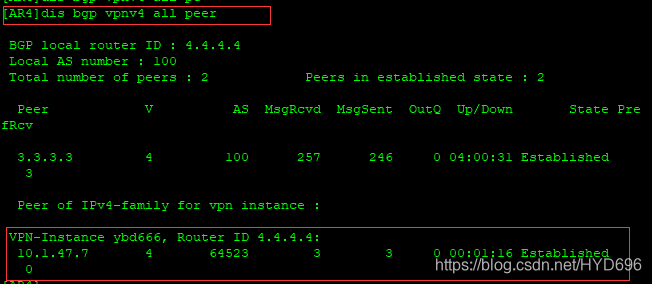
[AR2]isis 10
[AR2-isis-10]import-route bgp- 1
- 2
[AR4]dis bgp vpnv4 all routing-table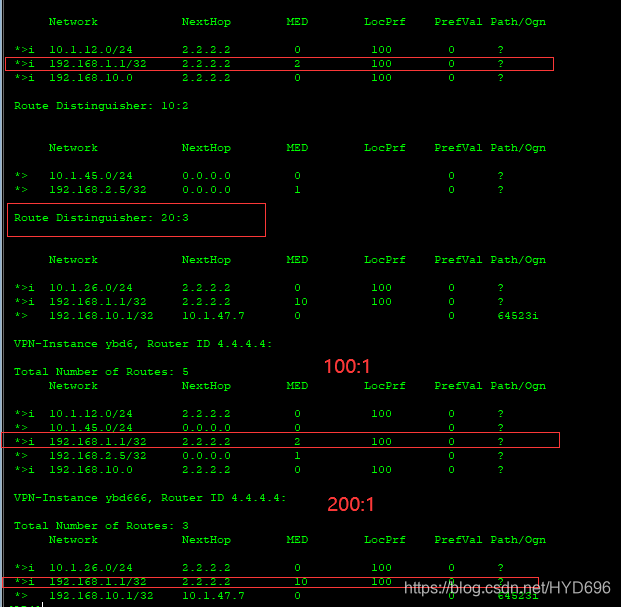
RD、RT不一样。
[AR2]dis mpls lsp
192.168.10.1 PING测 192.168.1.1
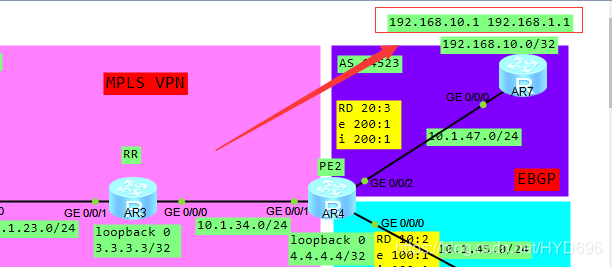
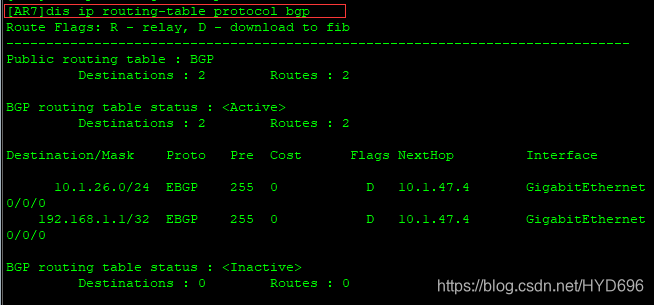
已学到192.168.1.1/32的路由,下一跳是10.1.47.4;
然后根据AR4的接口下绑定的ybd666路由表,去查找相关的路由。
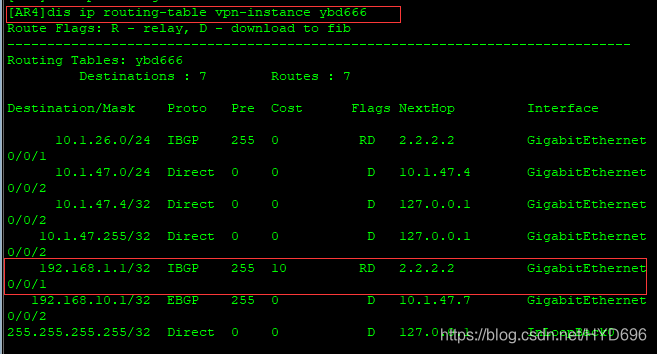
由以上输出结果可知,下一跳是2.2.2.2。
[AR4]dis bgp vpnv4 vpn-instance ybd666 routing-table 192.168.1.1
压入公网标签1024
弹出标签
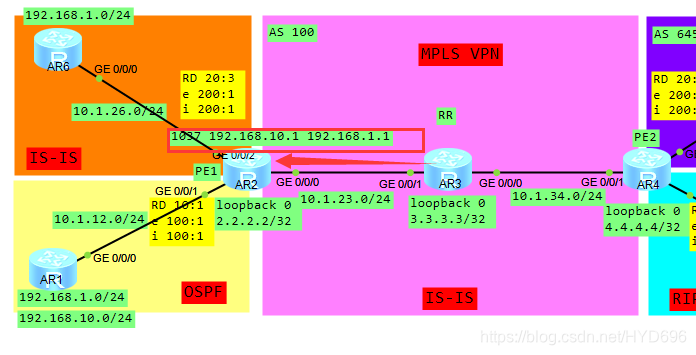
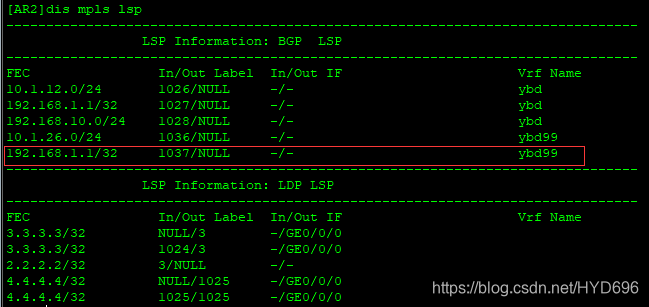
通过BGP协议得到的标签,收到的标签如果是1037的话,就属于ybd99路由表进行转发的。
192.168.1.1属于ybd99本地的报文
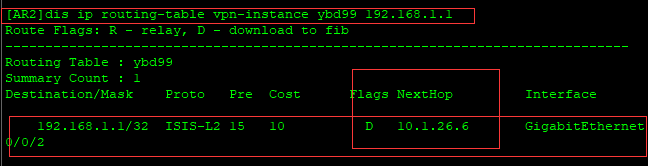
有以上输出结果可知,下一跳是10.1.26.6。
温故而知新,可以为师矣。

好了这期就到这里了,如果你喜欢这篇文章的话,请点赞评论分享收藏,如果你还能点击关注,那真的是对我最大的鼓励。谢谢大家,下期见!
- 分享
- 举报
 暂无数据
暂无数据-
浏览量:9183次2021-01-17 15:17:50
-
浏览量:8057次2021-01-19 02:00:45
-
浏览量:8039次2021-01-22 02:00:19
-
浏览量:6220次2021-01-15 01:14:50
-
浏览量:5250次2021-01-28 13:50:17
-
浏览量:4844次2021-01-19 20:10:23
-
浏览量:2031次2022-01-11 08:33:46
-
浏览量:5205次2021-09-07 13:36:59
-
浏览量:2093次2022-10-17 11:30:00
-
浏览量:1342次2023-04-17 15:56:29
-
浏览量:1960次2018-01-02 16:08:19
-
浏览量:5082次2021-04-20 16:55:59
-
浏览量:2022次2018-03-09 14:13:17
-
浏览量:790次2023-08-24 10:03:33
-
浏览量:1388次2018-03-07 14:59:18
-
浏览量:2572次2017-12-23 08:59:42
-
浏览量:1295次2019-06-06 13:16:23
-
浏览量:1612次2022-10-20 17:13:08
-
浏览量:2149次2022-10-19 11:34:08
-
广告/SPAM
-
恶意灌水
-
违规内容
-
文不对题
-
重复发帖
艺博东





 微信支付
微信支付举报类型
- 内容涉黄/赌/毒
- 内容侵权/抄袭
- 政治相关
- 涉嫌广告
- 侮辱谩骂
- 其他
详细说明


 微信扫码分享
微信扫码分享 QQ好友
QQ好友


